AWS infrastructure reference
When the AWS deployment target is selected, the HOP Command Line Interface tool (from here on, HOP CLI) will provision all the infrastructure needed for deploying the platform.
Cloudformation
For provisioning the infrastructure AWS Cloudformation is used. The stack definitions can be found in the HOP CLI’s GitHub repository:
Account stack: provisioning of resources that can be shared among different HOP applications.
Project stack: provisioning of resources that are project-specific and widely-used in different environments.
Local environment stack: provisioning of resources used when developing locally.
Cloud environment stack: provisioning of resources used in the testing and production environments. The stack is run once for each environment.
Provisioned architecture
The following picture shows the general architecture of the infrastructure provisioned by the HOP CLI.
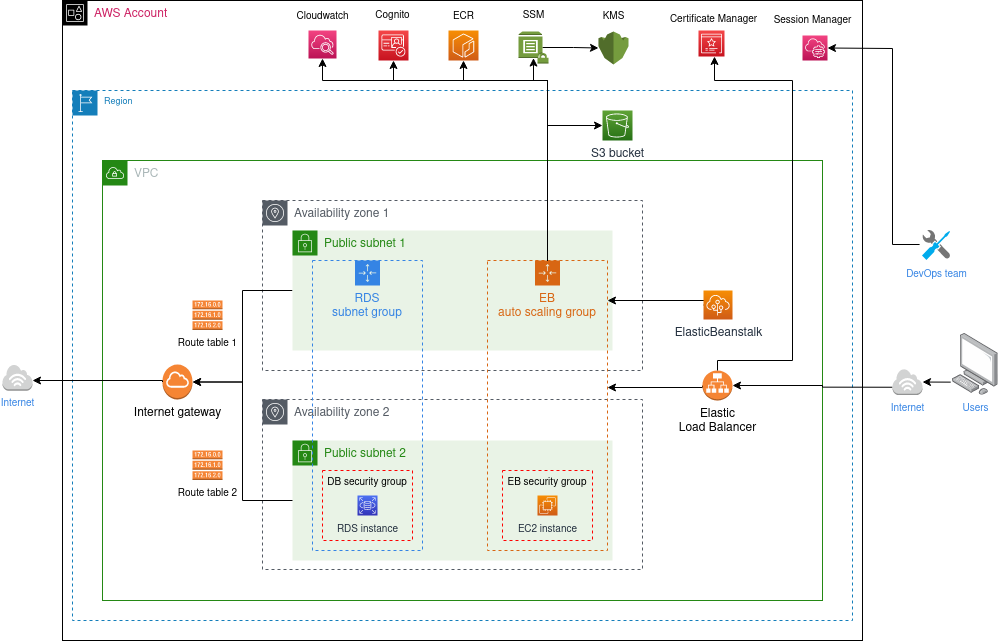
When creating the production infrastructure the following resources are shared with the testing environment:
VPC, Subnets and networking-related resources.
AWS Elastic Load Balancer.
AWS Elastic Container Registry.
Note
S3, RDS, Cloudwatch and Cognito resources are optional, and the user can choose to provision them or not in the settings file.
Security considerations
Inbound and Outbound traffic
The load balancer allows inbound HTTP traffic in port 80 and HTTPS in port 443.
HTTP traffic is redirected to HTTPS in the load balancer.
In order to access to the internal network (e.g., to connect to the RDS database instance from the local environment) AWS Session Manager must be used. No other inbound traffic is allowed.
Traffic from the public subnets to the Internet is allowed through the Internet Gateway.
IAM groups, users and roles
The following section lists the different group, users and roles created by the HOP CLI. The specific permissions attached to each entity can be consulted in the Cloudformation stack definitions.
IAM groups
<resource-name-prefix>-ci: group for the user(s) used to run Continuous Integration and Continuous Delivery pipelines.
IAM users
<resource-name-prefix>-ci: user for running the Continuous Integration and Continuous Delivery pipelines. It belongs to the<resource-name-prefix>-cigroup.<resource-name-prefix>-local-dev: user for assuming the development IAM role used in the development environment.
IAM roles
<resource-name-prefix>-rds-monitoring-role: role to allow the RDS instances to have enhanced monitoring.<resource-name-prefix>-aws-elasticbeanstalk-service-role: service role for the AWS Elastic Beanstalk applications.<project-name>-dev-role: role with access to the AWS resources used during local development. It will have more or less policies attached depending on the selected optional AWS services.<project-name>-<test/prod>-role: role to give access to the AWS resources to the testing and production environment AWS Elastic Beanstalk instances. It will have more or less policies attached depending on the selected optional AWS services. One role for each environment is created.